By Brian Olson, Director IBM Power Server and Security Solutions
Having worked with IBM i customers over the past 25 years, we have seen several trends that has impacted the security of the IBM i environment:
- Increasing use of network based services to access data on the IBM i system from inside the corporate network
- Increased connection of the IBM i based applications to the outside world
- Dramatic increases in cyber-crime, and the negative publicity and impact on corporate brand value, that these exploits can have
- Increased focus on, and enforcement of, regulatory compliance, whether SOX/CSOX, PCI or a variety of other standards
IBM i (or AS400 or iSeries if you prefer) has long been viewed as a highly stable and secure platform and as such, the security priorities (and budgets) of organizations have tended to be focused in other areas such Windows server/client platforms and external network access (firewalls). Compounding this, is a general lack of experience in the auditor community of the unique attributes of the IBM i environment, to the point where many audits only contain a cursory review of this platform, and usually from the 1,000 foot level.
Given the fact that the IBM i typically houses critical corporate applications and data, this general lack of attention paid by many organizations to IBM i security is a critical exposure for the hundreds (or thousands) of Canadian organizations that rely on this platform and its applications for their existence. Hence, here are some key tips that every IBM i customer organization should consider.
1. Log and monitor audit journal activity
The IBM i operating system provides audit journals that allow the logging of key system activity. Unfortunately, not all organizations have these audit journals enabled, and if they do, many do not monitor or report/alert on suspicious activity taking place. The sheer size and cryptic nature of these journals can make getting useful security information from this a challenge. Use 3rd party tools to provide this extra usability.
2. Implement exit programs to audit network-based activity
In the last 10-15 years, the use of TCP/IP based services (such as ODBC and FTP) to access data housed in the IBM i has grown exponentially. Traditional access to the AS400 has been through direct attached terminals and managed through menu access controls. OS400 (now called the IBM i operating system) provides exit points to allow this “external” access but does not adequately audit access through these services. 3rd party exit point solutions are a requirement to collect the necessary level of information to satisfy most auditor requirements.
3. Clean up inactive user profiles
Inactive user profiles are defined as profiles that have not been used in the last 30 to 60 days. A surprising number of IBM i shops have a large number of inactive profiles and these can pose a significant security exposure. Regular cleaning of inactive profiles should be a priority and there are tools available to help with the ease the administrative effort of this task and even provide some automated assistance.
4. Don’t confuse compliance with security
Your auditor might have told you that you have met compliance with your internal policies or regulatory policies, but this does not mean you are secure. Security is an ongoing process and mindset that does not end with a positive result on an audit. Understand where your key assets are, what poses the greatest business exposure to your organization, and be proactive in addressing these risks on an ongoing basis.
5. Audit power user profiles
Every organization has trusted power user profiles that have higher levels of access and control over your critical systems. However, it is exactly these user profiles that pose the greatest risk should they be compromised. Minimize the number of user profiles with these high authorization levels, and make sure you are auditing all activity on these profiles. These are the profiles that hackers love to get their hands on.
6. Implement and enforce strong password policies
Ensure that your password policies include frequent expiration of passwords, and the use of a reasonably strong password structure. Ensure you check for the use of default passwords because the IBM i operating system and many applications ship with standard defaults. Hackers love default passwords, so make sure you change them.
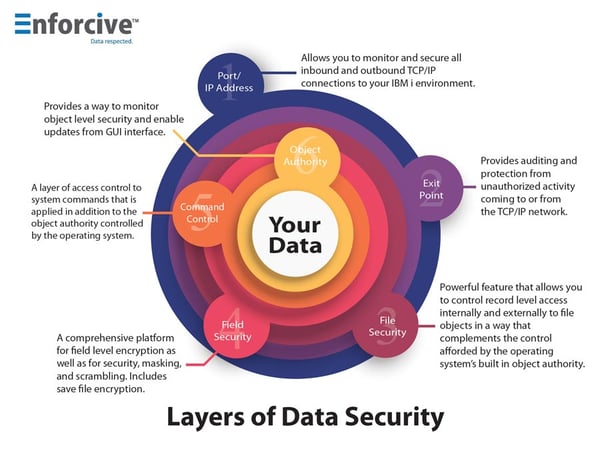
7. Use a layered approach to IBM i security
Security of any kind, is all about layering. If one layer gets compromised, the next layer should stop (or at least slow down) the attacker. Make it difficult for the hacker – they love “easy targets”. A single security approach is not enough, even within the IBM i platform. You wouldn’t secure your corporate network with just a firewall, would you?
Your IBM i should at least have strongly implemented object security, auditing of all activity, and even look at encryption for your highly sensitive data. Look at integrated solutions as a way of easing the administrative burden of managing all of these layers.
8. Automate security and compliance checking where possible
If security becomes onerous and difficult to manage, for most organizations, things begin to fall between the cracks, or get pushed off to be done “when you have time”. Automate your security practices where possible, or use tools to help ease the administrative burden. Run automated compliance checks for key security policies on a regular basis to ensure that you are still OK. Or if you are not, so you can correct the situation in a timely fashion. Again, 3rd party solutions are available to help you with this automation.
Able-One Systems can provide tools and expertise to help you with any, or all, of the above recommendations. We provide consulting services and products for security and compliance for IBM i, and offer a consulting service for IBM i Assessments called Verify for i. For more information, contact Brian Olson of Able-One at 800-461-2253 ext. 7316 or email brian.olson@ableone.com.



 more in the realm of user experience and deployment to multiple channels. Considerations for managing a range of user experiences today can include:
more in the realm of user experience and deployment to multiple channels. Considerations for managing a range of user experiences today can include:


