By Eden Watt, VP of Application Innovation, Able-One Systems www.futureday.ca/bio/
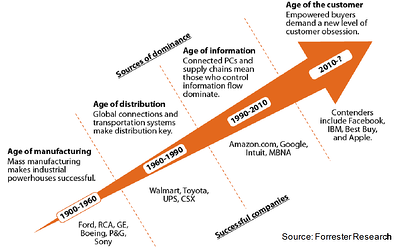 Advances in technology have transformed the way businesses operate and the way they interact with customers, prospects, and suppliers. While this has been evident throughout the history of Information Technology, the pace of change and effect on business is growing at an exponential rate.
Advances in technology have transformed the way businesses operate and the way they interact with customers, prospects, and suppliers. While this has been evident throughout the history of Information Technology, the pace of change and effect on business is growing at an exponential rate.
Software is no longer just a cost centre; it has become a strategic commercial advantage (or disadvantage). In today’s high-tech world, innovation and new business processes can typically only be accomplished with the assistance of new software or by updating, changing or extending existing software.
This means that flexibility with enterprise software can be a major, differentiating factor for organizations that need to rapidly innovate in our increasingly competitive world.
Four key ‘disruptors’ or game changers are driving the current need to innovate:
- Mobile – consumers now have access at their fingertips all the time. This is necessitating continuous evolution of employee, customer, partner, and prospect interactions and integration with core systems.
- Social Business – customer interactions are coming from new and emerging channels, many of which businesses can no longer control. To be a leader today, organizations must engage in these new areas.
- Cloud – the ability to deploy everything from hardware\infrastructure to software and services in the virtual world is changing the way IT can deliver and the way users behave. The considerations and possibilities are endless but how do you decide the most secure, cost-effective, flexible approach for your enterprise systems?
- Big Data – An unprecedented amount of data can be collected today on everything, including customer behaviour, location, travels, and buying habits but how do you sift through it all to introduce more advanced application capabilities that will affect the bottom-line?
With the emergence of these four key disruptive technologies, there are more empowered users with expectations for higher quality customer experience. Meeting these requirements with the additional situation of a volatile world economy and tighter control over budgets and resources plus ongoing regulatory changes and demands is a significant challenge that IT must face today.
 But meeting these challenges can be especially complex for organizations managing traditional business systems that were implemented before these ‘disruptors’ were in play. Some enterprise systems may even be decades-old and considered legacy but regardless, the day to day business depends on them and they are typically very rich in functionality and not easily replaced.
But meeting these challenges can be especially complex for organizations managing traditional business systems that were implemented before these ‘disruptors’ were in play. Some enterprise systems may even be decades-old and considered legacy but regardless, the day to day business depends on them and they are typically very rich in functionality and not easily replaced.
So the need to adapt traditional systems so that business can react to the advanced needs of today’s technology savvy consumer and leverage current capabilities is at the heart of where Information Technology needs to focus so that IT can lead the business to new frontiers and remain competitive.
In future posts, we will explore these challenges in greater detail and discuss how to overcome them.
Also coming up on November 26th, we will be hosting the “IT is Business, Business is IT” Event at Entertaining Elements in Kitchener, Ontario. Join guest speakers from Able-One and IBM for appetizers and drinks, and a special presentation where you will learn how your IT drives business agility. To ensure you receive information about this event and how to register, please send an email to events@ableone.com.


 Advances in technology have transformed the way businesses operate and the way they interact with customers, prospects, and suppliers. While this has been evident throughout the history of Information Technology, the pace of change and effect on business is growing at an exponential rate.
Advances in technology have transformed the way businesses operate and the way they interact with customers, prospects, and suppliers. While this has been evident throughout the history of Information Technology, the pace of change and effect on business is growing at an exponential rate. But meeting these challenges can be especially complex for organizations managing traditional business systems that were implemented before these ‘disruptors’ were in play. Some enterprise systems may even be decades-old and considered legacy but regardless, the day to day business depends on them and they are typically very rich in functionality and not easily replaced.
But meeting these challenges can be especially complex for organizations managing traditional business systems that were implemented before these ‘disruptors’ were in play. Some enterprise systems may even be decades-old and considered legacy but regardless, the day to day business depends on them and they are typically very rich in functionality and not easily replaced.