By: Gavriel Meir-Levi, Enforcive Inc and Brian Olson, Able-One Systems Inc.
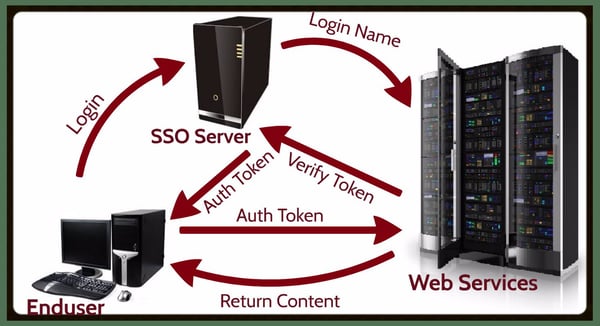
In order to ease the password management experience for their end-users, many enterprises are considering implementing Single Sign-On (SSO). SSO provides many benefits, such as requiring a user to only sign on once in a multi-server environment. SSO server becomes the “keeper of the keys” of your IT estate.
Challenges of Single Sign-On
The challenging aspect of SSO is that implementation usually takes a couple of months and requires considerable investment of staff hours and capital. The other major problem with SSO, is that it creates a single point of failure both in terms of system resiliency and security. If your SSO server fails or is compromised, EVERYONE IS IMPACTED!
Imagine a castle where the draw-bridge fails. Worse yet, if your SSO server gets compromised, it has all of your organization’s credentials. Single sign-son’s greatest strength is also its greatest weakness; single point of failure.
Password Self-Service
Password Self-Service by Enforcive takes a different approach. Instead of locking all of the passwords up in a single sign-on castle, Password Self Service creates a resilient on-going password management strategy that’s more like an EZ Pass to a city’s roads, bridges and tunnels or a passport that allows you to travel throughout Europe.
Password Self Service does not store any of your passwords locally, it just synchronizes and monitors them throughout all of your systems; IBM i, AIX, Linux, Windows AD, OpenLDAP and others. The passwords stay exactly in the same place they were before PSS was installed, thus solving the single point of failure problem.
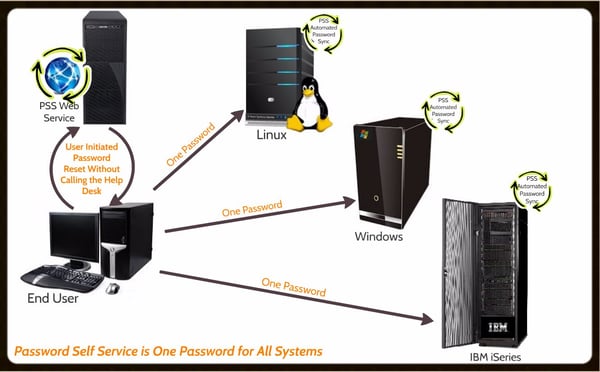
Empowering your end users is a crucial piece of this puzzle. You do not want your Help Desk getting that 2AM call from the CEO who is in Indonesia getting ready for a meeting and is literally locked out of everything.
Integrating Password Self-Service
If you run IBM iSeries as well as Windows servers, setting up the IBM i server to interface with Windows Active Directory is relatively easy, creating single sign-on functionality between Windows and the iSeries. This solves the problem of having to sign on separately for Windows and the iSeries.
From a password management perspective, once you bring the Help Desk into the equation, things get a bit trickier. Your iSeries team will have to make a difficult choice to:
- Give the Help Desk SECADMIN privileges, or
- Turn your iSeries support staff into the Help Desk
Neither option is particularly attractive. Giving your users the power to reset their own passwords eliminates this issue.
In terms of implementation, while SSO often turns into a complex and costly project, Password Self Service by Enforcive can be implemented in a manner of days. It provides critical help for your Help Desk by enabling your end-users to securely reset their own passwords 24/7, vastly improving your organization's ROI in terms of Help Desk staffing and resources.
PSS uses challenge questions, secure tokens and an authentication server call to make sure your end-user is who they say they are and administrators have great flexibility in how they implement the tool. Once an end-user has been validated, passwords can be synchronized so that they only have to remember one password.
Empowering your end users to better and more seamlessly manage their credentials while enabling access for different parts of your IT estate without creating a single point of failure is a great way to harden security, improve user experience and help your Help Desk.
Contact Brian Olson of Able-One at brian.olson@ableone.com or 519-570-9100 ext 7316 for more information or to set up a PSS demonstration webinar for you today.